My Cisco Anyconnect VPN Client keeps on disconnecting after I changed my laptop and upgraded to windows 10. My internet connection is same and it was working fine on my previous laptop. In Device Manager under Network Adapter I see a warning sign on my Microsoft Wi-Fi Direct Virtual Adapter. I have a user reporting that when they connect to the VPN they loose their internet connection. They can still access company intranet. We use Cisco anyconnect to access the VPN. They are using Windows 7. Full disclosure. This is my first VPN troubleshooting ticket. A replacement has been fitted and configured the same as the failed unit but now we are unable to get a connection using Cisco AnyConnect. As soon as the AnyConnect establishes a connection the internet connection drops on the PC. The AnyConnect client still thinks it is connected.
In my experience with TM 1300 in D600 XP Pro, wireless connection via TM 1300 works perfectly fine via any WiFi AP or Router, but when I open Cisco VPN client(VPN 5000 Client 5.2.3 3DES, old and EOF vpn box but no $ to upgrade) via WiFi I lose both internet/VPN connection in about 10 minutes or so. This is not to be confused with the AnyConnect reconnect functionality for persistence of an existing VPN session across connection failures or loss of a network interface. When 'Always On' is disabled, the work-around is to simply exit the GUI and start over (though this should not be necessary).
Some VPNs allow split tunneling, however, Cisco AnyConnect and many other solutions offer a way for network administrators to forbid this. When that happens, connecting to the VPN seals off the client from the rest of the LAN. As it turns out, breaking this seal is not that hard, which can be useful for special cases like performing pentests over a VPN designed for average users.
In our case, we had to use a hardware token that only had drivers for Windows and Mac, while most of our tools run best (and are already installed) on Linux. We started investigating on both supported platforms mentioned above and found
what others have already discovered: the routing table is modified (and kept in this state), while packets are further filtered, probably using kernel hooks.
Both IPv4 and IPv6 are affected by this filtering, and traffic towards additional network interfaces also got redirected. So we embarked on a quest to find what could be done within the rules imposed by the VPN vendor. Our first stop was the gateway in our LAN towards the internet – and thus towards the VPN concentrator. The VPN client explicitly installed routes to keep that reachable, however, packets sent directly towards the LAN gateway never arrived there, leading us towards the idea of further kernel-based filters.
The next idea was the VPN server itself since it had to be able to receive packets from the clients as part of normal operation. However, the question is: how can you tell the packets apart on the gateway – as you still have to forward packets that are part of the normal VPN operator towards the VPN server. The trivial way was TCP port numbers, so we tried connecting to various TCP ports on the VPN server, but the gateway saw no SYN packets.
This left us with a single opportunity: keeping even the TCP port the same as the port used by the tunnel already. As netstat has shown, a TCP connection towards port 443 was kept open throughout the VPN session, and subsequent connections were allowed by the
filtering mentioned above – we could even see these SYN packets on the gateway. The only problem was to tell TCP streams apart at the gateway so that the VPN still worked while we could initiate connections outside of it at the same time.
And then it clicked: while trying to cope with the fact that many public (or semi-public) Wi-Fi networks filter everything besides TCP/443 (HTTPS), we had SSLH deployed to multiplex HTTPS and SSH on the same TCP port. This works reliably because they are really easy to tell apart upon the first packet:
- SSH clients send plain text one-liners that identify the protocol and client version, while
- SSL/TLS clients send binary Client Hello packets that identify the protocol version and supported ciphers.

SSH fits this case since its port forwarding features makes it possible to punch as many holes as necessary, regardless of the direction (VPN to LAN vs. LAN to VPN).
On Debian and its derivative systems, SSLH can be installed simply from the package with the same name (sslh) and configuration can be found in the file /etc/default/sslh as a command line, as this is where SSLH takes its options from. Below is the significant line:
This just means that SSLH listens on the internal (LAN) IP address of the gateway and based on the first packet received from a client that reaches this port, it either forwards it to
- a local SSH server (here we had the VPN client running on a Windows VM, and the Linux host had the SSH daemon running, hence the variable name
$VM_HOST_IP) or - the original VPN server.
Changes to the options can be applied under Debian and its derivatives by running /etc/init.d/sslh restart and the results can be tested in isolation first by connecting to TCP port 443 of the gateway, which should behave like the VPN server when using a TLS client like openssl s_client and act as an SSH server when using OpenSSH or PuTTY.
When all this works, the last bit is to redirect traffic towards the VPN server to SSLH. One way is using NAT functionality from iptables:
This command adds a rule to the chain called PREROUTING within the nat table, where packets arrive before the routing decision happens. The next part is the filter, which is important to avoid loops: we only apply the magic to packets where the network interface that the packet arrives through is the LAN interface. The rest narrows the filter further to the destination TCP port being 443 and the destination host being the VPN server. The last part is what happens when this rule matches: we invoke the REDIRECT target that rewrites
- the destination host to the IP address of the interface the packet arrived through (here: LAN interface) and
- the destination port to the one supplied (here: 443).
Since SSLH was configured to listen on TCP port 443 on the LAN interface, this results in the same effect as in the above SSLH testing scenario, where we connected directly to TCP port 443 on the gateway. And the best part is that the NAT solution provided by iptables is fully bidirectional, reply packets from SSLH are automatically translated back to make it seems as if they were sent by the VPN server.
So with the iptables rule in place, everything is ready for a real-life test. The progress of SSLH can be followed in syslog and as it can be seen below, after the AnyConnect client has connected properly, SSH connections can also get through, and everything gets routed to its proper destination.
When you are off campus, some of Illinois State University’s electronic services are unavailable to you unless you establish a VPN connection.
Cisco Anyconnect Disables Internet Connection
Cisco AnyConnect is an application that the University makes available to students, faculty, and staff for free which may be used to establish a VPN connection with the University from off campus.
NOTE: If you need to request and install the application on your computer, please skip to the section further below entitled Download and Install Cisco AnyConnect. If you already have the application installed and would like to know how to connect to it, please read the section immediately below entitled Connect to the Cisco AnyConnect VPN Client Once Downloaded. The instructions below are listed for both Windows and Mac machines, respectively.
Connect to the Cisco AnyConnect VPN Client Once Downloaded
Windows:
- Open the Cisco AnyConnect VPN client.
- Windows 8: On the Start screen, click Cisco AnyConnect Secure Mobility Client.
- Windows 10: Start > All Apps > Cisco > Cisco AnyConnect Secure Mobility Client.
- Alternatively, you can click Start and begin typing Cisco AnyConnect Secure Mobility Client and the application will show up. Click on the icon to start the application.
- Verify that the path in the field underneath “Ready to connect.” is VPN01.ILSTU.EDU.
- If the path name does not automatically appear, click the arrow to the right of the field and select VPN01.ILSTU.EDU from the drop down menu, or enter the path name manually.
- Click Connect.
Figure 1:
- When prompted, select the appropriate Group (Figure 1):
- To access most ISU resources, you will select –ISU-.
- Important: To access ISU Oracle or SQL database resources directly (via software such as Microsoft Access, Oracle SQL Developer, Microsoft SQL Management Studio, etc.), select DB-User_Access.
Note: When you attempt to connect, you may receive a prompt that tells you that Cisco AnyConnect is updating. Do not attempt to cancel this update, as this update will allow your VPN software to work.
Figure 2:
- Enter your ULID and password in the appropriate fields, then click OK.
- After a moment, an informational banner window will appear that typically says “Welcome to Illinois State University,” but could display a different, informational message.
- Click Accept.
You are now connected with the Cisco AnyConnect VPN client. A Cisco AnyConnecticon with a yellow, locked padlock will be visible in your system tray (in the lower-right corner of your desktop, next to the clock). This indicates that you are connected. If the icon appears without a padlock, this indicates you are no longer connected through VPN.
Mac OS X:
- Open the Cisco AnyConnect VPN client. Click Finder > Applications> Cisco > Cisco AnyConnect Secure Mobility Client.
Figure 3:
- Alternatively, you can search for the application in your “Dashboard” by simply clicking the rocket icon on your bottom toolbar. After that, start typing Cisco AnyConnect Secure Mobility Client and you will see the application. Click on the application to start the set-up process, or to access it once you’ve configured the settings properly.
Figure 4:
- Verify that the path in the field underneath “Ready to connect.” reads VPN01.ILSTU.EDU. If the field is empty, you will need to manually enter the file path exactly how it is shown in this article.
Figure 5:
- Click Connect.
- When prompted, select the appropriate Group (Figure 6):
- For most ISU resources, you will select –ISU-.
- Important: To access ISU Oracle or SQL database resources directly (via software such as Microsoft Access, Oracle SQL Developer, Microsoft SQL Management Studio, etc.), select DB-User_Access.
Figure 6:
- Enter your ULID and password when prompted to do so and click Connect.
- After a moment, an informational banner window will appear that typically says “Welcome to Illinois State University,” but could display a different, informational message.
- Click Accept.
You are now connected with the Cisco AnyConnect VPN client. A Cisco AnyConnect icon with a yellow, locked padlock is now in your system tray (in the lower-right corner of your desktop). This indicates that you are connected. If the icon appears without a padlock, this indicates you are no longer connected through VPN.
Disconnect from the VPN
Windows:
To disconnect from the VPN on a Window’s machine:
- Locate the Cisco AnyConnect VPN client icon and click on it. It is usually on your toolbar, but if it is not, here are some additional ways to find the application:
- Windows 8: On the Start screen, click Cisco AnyConnect Secure Mobility Client.
- Windows 10: Start > All Apps > Cisco > Cisco AnyConnect.
- Alternatively, you can click [Start] and begin typing Cisco AnyConnect Secure Mobility Client and the application will show up. Click on the icon to start the application so you can disconnect from the VPN.
- In the Cisco AnyConnect Secure Mobility Client pane, click Disconnect.
Figure 7:
- Close Cisco AnyConnect Secure Mobility Client.
You are now disconnected from VPN.
Mac OSX:
To disconnect from a VPN connection on Cisco AnyConnect on Mac running Mac OS X or later:
- Click on the Cisco AnyConnect icon in your Dock.
- Click Disconnect.
- Close Cisco AnyConnect Secure Mobility Client.
Figure 8:
You are now disconnected from VPN.
Download and Install Cisco AnyConnect for Windows or Mac OS X
Students, faculty, and staff may download the Cisco AnyConnect VPN Client for Windows or Mac OS X from the University IT Help portal by following the directions below:
Windows:
- Navigate to the IT Help portal (at ITHelp.IllinoisState.edu),
- Click Downloads in the middle of the screen.
- Under Cisco AnyConnect, select the version you would like to download. You will need to select the version that is compatible with your machine. You can choose either Windows or Mac.
- Click on Windows or Mac and log in with your ULID and password if prompted to do so. You will be directed to a form to request the download file be sent to you. You will need to fill out the required fields in the submission form. Once submitted, your request will be handled in the order it was received. Once approved, you will receive an email. You will then click Download Files and you may be navigated to a Central Login page where you will need to enter your ULID and password. Once you log in, click the file next to Attached Files.
NOTE: If you have never access Liquid Files (SendTo) before, you may see a log in page to log into Liquid Files itself. Instead, you will want to click the SSO Sign In button to be navigated to a Central Login page. You will enter your ULID and password. Upon logging in, you will need to accept some terms and conditions. Once you have done that, you will never be prompted again for an SSO sign in.
- Upon successfully downloading the installer, you will need to open the installer and follow the prompts.
Figure 9:
- Agree to the Terms and Conditions and proceed with the installation by clicking Accept. You may need to enter your computer’s profile credentials in order to accept the installation.
Figure 10:
- Once the software has finished downloading, click Finish to close out of the installation process. You can now access the VPN software.
Cisco Anyconnect Vpn Stops Internet Connection In Windows 10
Mac OS X:
- Navigate to the IT Help portal (at ITHelp.IllinoisState.edu),
- Click Downloads in the middle of the screen.
- Under Cisco AnyConnect, select the version you would like to download. You will need to select the version that is compatible with your machine. You can choose either Windows or Mac.
- Click on Windows or Mac and log in with your ULID and password if prompted to do so. You will be directed to a form to request the download file be sent to you. You will need to fill out the required fields in the submission form. Once submitted, your request will be handled in the order it was received. Once approved, you will receive an email. You will then click Download Files and you may be navigated to a Central Login page where you will need to enter your ULID and password. Once you log in, click the file next to Attached Files.
NOTE: If you have never access Liquid Files (SendTo) before, you may see a log in page to log into Liquid Files itself. Instead, you will want to click the SSO Sign In button to be navigated to a Central Login page. You will enter your ULID and password. Upon logging in, you will need to accept some terms and conditions. Once you have done that, you will never be prompted again for an SSO sign in.
- Upon successfully downloading the installer, you will need to open the installer and follow the prompts. When you get to the Installation Type screen, ensure that only the VPN checkbox is selected, then click Continue to proceed with the installation
Figure 11:
- Click Continue to finish the installation. Once finished, open the Cisco AnyConnect Secure Mobility Client. You can find it in the Cisco folder in your applications, or can be manually searched in your Launchpad, as instructed above.
Figure 12:
Cisco Anyconnect Disables Internet Connection Code
- Type VPN01.ILSTU.EDU in the empty text field, then press Connect.
Figure 13:
- Enter your ULID in the Username field and your current password in the Password field. Click OK.
Figure 14:
- You will see a welcome window. Click Accept to be connected to the VPN.
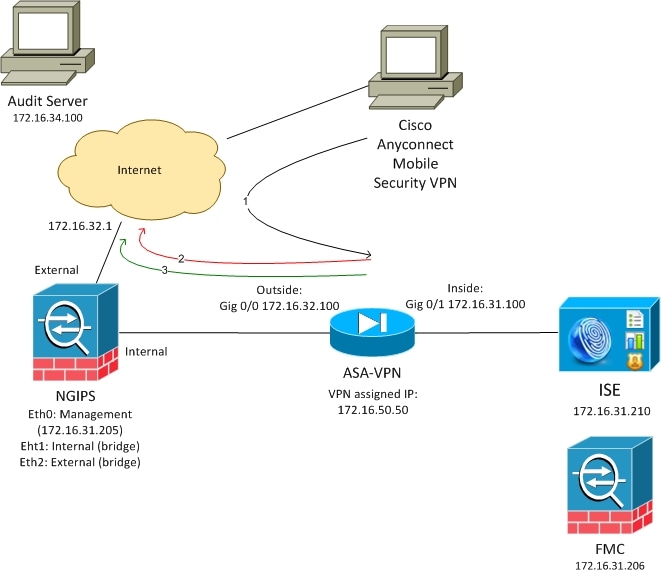
Figure 15:
- Now that you are connected, you will be able to access university-restricted applications such as iPeople.
- When you are ready to disconnect from the VPN, go back to the application and click Disconnect and close out of the application.
Cisco Anyconnect Disable Ipv6
Figure 16:
How to Get Help
For technical assistance, you may contact the Technology Support Center at 309-438-4357 or by email at SupportCenter@IllinoisState.edu.
Back to Overview:
Related Articles:
